
If your organization handles protected health information, preparing for a HIPAA compliance audit is not optional. Whether you are a healthcare provider, health plan, clearinghouse, or business associate, HIPAA requires you to safeguard patient data and prove that your controls work.
A HIPAA audit can feel overwhelming due to strict requirements, detailed documentation, and the risk of fines. However, with the right preparation and a clear understanding of the process, HIPAA compliance becomes manageable and repeatable.
This guide explains what a HIPAA compliance audit is, when audits happen, how the audit process works step by step, and how to prepare your organization for long-term compliance.
- What Is a HIPAA Compliance Audit?
- When and Why You Need a HIPAA Compliance Audit
- The HIPAA Compliance Audit Process in 8 Steps
- Step 1: Assign Roles and Define Audit Scope
- Step 2: Conduct a HIPAA Risk Assessment
- Step 3: Gather and Review Required Documentation
- Step 4: Validate Administrative, Physical, and Technical Safeguards
- Step 5: Review Audit Logs and Monitoring Practices
- Step 6: Interview and Observe Key Personnel
- Step 7: Report Findings and Create a Remediation Plan
- Step 8: Re-Audit and Maintain Ongoing Compliance
- HIPAA Audit FAQs
- Conclusion
What Is a HIPAA Compliance Audit?
A HIPAA compliance audit is a formal review of an organization’s policies, procedures, and technical safeguards used to protect protected health information (PHI) and electronic protected health information (ePHI).
The audit evaluates compliance with the HIPAA Privacy Rule, Security Rule, and Breach Notification Rule. Auditors assess whether required administrative, technical, and physical safeguards are properly implemented and followed in day-to-day operations.
HIPAA audits may be conducted internally, by an independent third party, or by the Office for Civil Rights (OCR), which enforces HIPAA under the Department of Health and Human Services (HHS).
When and Why You Need a HIPAA Compliance Audit
Organizations undergo HIPAA audits for several reasons.
Ongoing Risk Management
HIPAA requires covered entities and business associates to perform regular risk assessments. Internal audits help identify gaps before they lead to data breaches, regulatory penalties, or patient harm. Civil penalties for HIPAA violations can reach tens of thousands of dollars per violation, even when noncompliance is unintentional.
Customer and Partner Requirements
Many healthcare organizations require vendors and service providers to demonstrate HIPAA compliance before signing contracts. Audits and documented controls help establish trust and satisfy due diligence requirements.
OCR Enforcement Audits
The OCR conducts audits as part of its enforcement program. Organizations may be selected randomly or after a reported breach. Being audited does not automatically mean wrongdoing, but participation is mandatory once selected.
Regular internal audits ensure your organization can respond quickly and confidently if OCR initiates an investigation.
Turn compliance into a growth advantage.
Get expert help building a scalable security and compliance program without slowing down your team.
The HIPAA Compliance Audit Process in 8 Steps
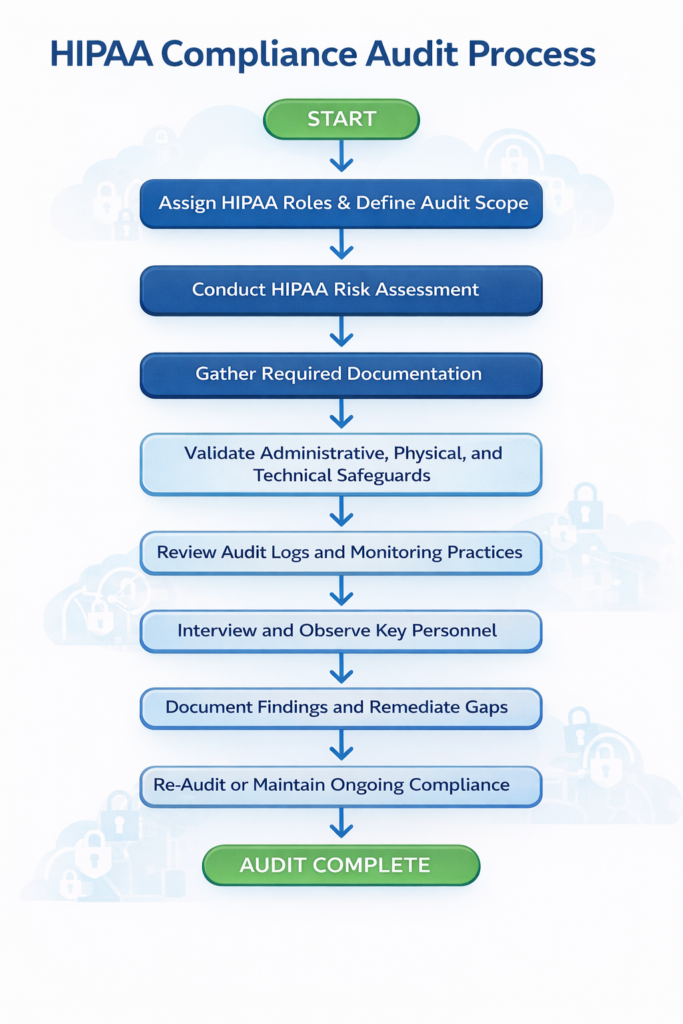
Step 1: Assign Roles and Define Audit Scope
HIPAA requires organizations to appoint a Privacy Officer and a Security Officer. These roles oversee compliance, training, incident response, and audit coordination.
Next, confirm your HIPAA classification.
- Covered entities include healthcare providers, health plans, and clearinghouses
- Business associates include vendors that create, receive, maintain, or transmit PHI on behalf of covered entities
Finally, define the audit scope. Include all systems, locations, devices, vendors, and personnel that interact with PHI or ePHI. Physical media and remote access environments should also be included.
Step 2: Conduct a HIPAA Risk Assessment
A HIPAA risk assessment identifies vulnerabilities that could lead to unauthorized access, disclosure, or loss of PHI.
Key activities include:
- Identifying systems that store or transmit PHI and ePHI
- Mapping PHI data flows across systems and vendors
- Reviewing administrative safeguards such as policies and workforce training
- Evaluating technical safeguards including access controls, encryption, and patching
- Assessing physical safeguards such as workstation security and device storage
Risk assessments must be documented and updated regularly, especially after system changes or incidents.
Step 3: Gather and Review Required Documentation
HIPAA compliance relies heavily on documentation. Auditors expect written evidence showing that policies exist and are followed.
Common documentation includes:
- HIPAA policies and procedures
- Risk assessment reports
- Workforce training records
- Business Associate Agreements
- Incident response and breach notification plans
- Access logs and system audit logs
- Data retention and disposal policies
Missing or outdated documentation is one of the most common audit findings.
Step 4: Validate Administrative, Physical, and Technical Safeguards
Auditors test whether safeguards work in practice.
Administrative safeguards include workforce training, sanctions, and policy enforcement.
Physical safeguards include facility access controls and device security.
Technical safeguards include encryption, multi-factor authentication, access logging, and malware protection.
Controls must align with the risks identified in your risk assessment and be consistently enforced.
Step 5: Review Audit Logs and Monitoring Practices
HIPAA requires organizations to monitor system activity involving ePHI. Audit logs track logins, file access, changes, and system events.
Logs should be reviewed regularly and retained for at least six years, unless state laws require longer retention. Effective monitoring helps detect suspicious behavior early and supports breach investigations.
Step 6: Interview and Observe Key Personnel
Auditors may interview staff to confirm they understand HIPAA policies and follow procedures correctly.
This step often reveals gaps between documented policies and real-world behavior. Training deficiencies, unclear procedures, or workflow obstacles are common root causes of noncompliance.
Employees should also understand how to report security incidents and suspected breaches.
Step 7: Report Findings and Create a Remediation Plan
After completing the audit, document findings in a formal report. Each issue should be evaluated based on likelihood and potential impact.
Create a remediation plan that assigns ownership, timelines, and corrective actions. Track progress and retain documentation showing that issues were addressed.
Audit reports should be retained for future audits and regulatory reviews.
Step 8: Re-Audit and Maintain Ongoing Compliance
HIPAA compliance is continuous. Annual audits are a best practice, and organizations with prior findings should re-audit after remediation.
Continuous monitoring, regular access reviews, updated risk assessments, and workforce training help maintain compliance between audits and reduce audit fatigue.
Ready to move forward with confidence?
We help teams build security programs that customers trust.
HIPAA Audit FAQs
How often should organizations perform HIPAA audits?
HIPAA requires regular risk assessments. Most organizations perform internal audits annually, though higher-risk environments may audit more frequently.
Who can perform a HIPAA compliance audit?
Organizations may conduct internal audits, hire third-party auditors, or be audited by OCR. OCR audits are mandatory once initiated.
What triggers an OCR HIPAA audit?
Audits may follow data breaches, complaints, or be part of OCR’s random audit program. Any covered entity or business associate may be selected.
What does an OCR HIPAA audit include?
OCR audits assess compliance with the Security Rule and Breach Notification Rule. The Privacy Rule is also evaluated when applicable.
Can startups and business associates be audited?
Yes. HIPAA applies regardless of company size. Startups and business associates are fully subject to OCR audits.
Conclusion
Preparing for a HIPAA compliance audit does not have to be overwhelming. By understanding your responsibilities, regularly assessing risk, maintaining clear documentation, and monitoring safeguards, your organization can stay compliant and audit-ready year round. A proactive approach not only reduces regulatory risk but also strengthens trust with patients, partners, and healthcare customers who depend on you to protect sensitive health information.
